
Blockchain technology is predicted to get over $1 trillion by 2032, according to a market research prognosis, focusing on blockchain for particular business segments.
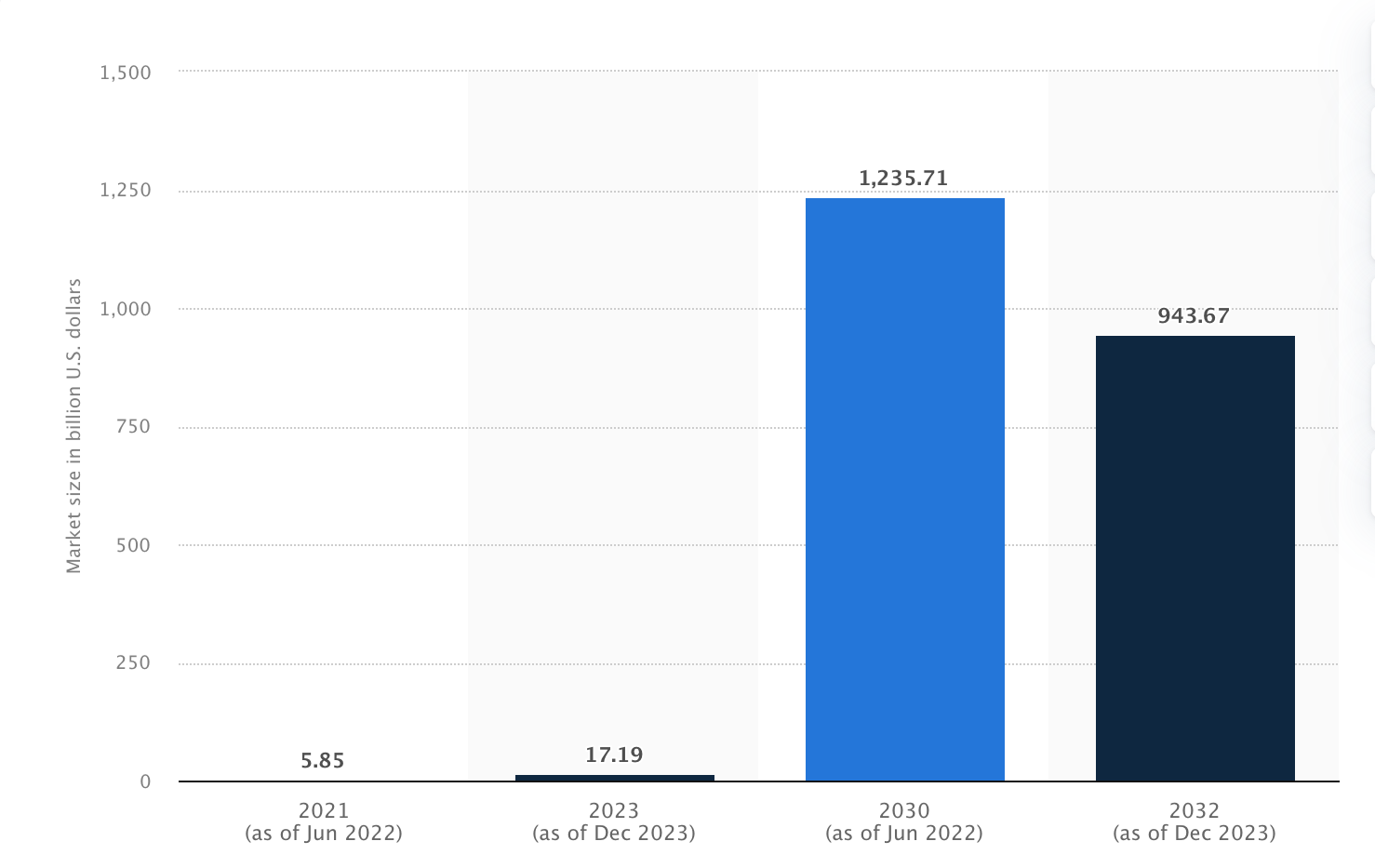
Blockchain technology cloud market size, with a prognosis for 2030, Statista
This is somewhat awaited because blockchain developer teams have found a wide use variety for decentralization—in gaming, real estate, logistics, medical care, and finance.
One of the explanations for this upsurge is that technology is often characterized as being extremely secure. But what stands behind it?
One of the central components adding to blockchain safeness is a hash that meets the encrypted requirements needed to protect information.
What Is a Hash? Definition, Explanation, and Role in Blockchain
Blockchain hashing is a process that takes any kind of data—a file or transaction—and turns it into a fixed-length cord of special symbols.

The resulting cord is known as the hash value, a unique representation of the input data irrespective of its size. It doesn’t matter if you hash a small text or a highly detailed transaction record; the output of hashing will always be of the same length.
The hash value is often called a “digital fingerprint.” The nature of this fingerprint is such that, with only one changed bit of the original data, it will produce a completely different hash.
The most common hash function applied in the blockchain is SHA-256 or Secure Hash Algorithm-256 bit. It becomes the basic building block for anyone who wants to develop a blockchain solution because it provides wholeness and safeness to data.
Other hash functions include but are not limited to MD5 and SHA-3; however, each has different prerequisites for security, and hence not all of them would be strong enough to be applied for blockchain purposes.
Some Basic Facts About Hashes
One of the most important roles in secure blockchain technology is played by hashes, and the reason they are so influential is due to a number of their properties:
Fixed-Length Output
No matter how big or small the input data is, the hashing technology will always generate a result of a fixed length. For instance, SHA-256 produces a 256-bit hash whether you’re hashing a single word or an entire document.
Predictable
The selfsame input will always let out the identical hash. Because of this sameness, blockchain systems can verify data through hash comparisons. If even a single figure in the input changes, the hash becomes completely different.
Collision-Resistant
No two different portions of data should ever create the same hash. In other words, it means that each input of data has a unique “digital fingerprint,” thereby reducing any possibility of collision—a situation where two identical hashes occur.
Non-Reversible
Hashing is a one-way function because it is rather easy to create a hash from data, but impossible to recreate from the hash what the original data was.
How Blockchain Hashing Fortifies Security
As we mentioned above, blockchain hashing creates a digital fingerprint for any piece of data, which makes it easy to hold data integrity.

Even replacing one letter of the data will totally alter the result. In such a way, it is rather easy to notice the attempt at tampering with the data—it only has to be checked if the hash matches.
Hashing also creates a level of trust in a blockchain system, with everything being verifiable through the hash. There is no need for a central authority to investigate every transaction because participants can independently verify that data is correct.
Hashing finally plays an important role in the so-called Proof of Work, a mechanism used on most blockchains, including the first-introduced Bitcoin.
The miners in PoW are tasked with solving a challenging puzzle by finding a hash that meets certain criteria.
The computing power exerted in solving such problems is enormous, and for this reason, tampering with a blockchain becomes very difficult since all that work would have to be redone for each block by any user who so desires.
How Hash Technology Works in a Blockchain: Real-World Example
Suppose a user sends 2 Bitcoins to someone. The transaction details, such as sender and receiver, along with the amount transferred, are added to a block of many other transactions.
This block also contains some extra details, such as a record of the time and a ref to the foregoing block.
Next, the entire block is run through a hash function (like SHA-256), which creates a unique hash value.
How it works: blocks link in such a way that each block has its hash and the hash of the previous block. That is, Block 1 has its own hash, and Block 2 contains its hash and a reference to Block 1’s hash.
Block 3 contains its hash and Block 2’s hash, and so on. It forms a chain of blocks in a secured manner—hence the name “blockchain”.
Now, if someone tries to change the data in Block 1 (for example, altering the amount in a transaction), the hash for Block 1 will change. Since Block 2 leans on Block 1’s hash, it will no longer match, which breaks the chain.
To hide the intervention, the attacker would then need to rehash Block 1 and every block thereafter, which is a ridiculously high computation condition.
Limitations and Counterarguments of Blockchain Hashing
While powerful, hashing does not come without its problems. First off, these can be collision attacks, meaning that two different data produce the same hash though this could happen very rarely with modern hash functions such as SHA-256.

Theoretically, it is still a risk. Experts in cryptography keep working hard to make even safer hash functions, to avoid collisions.
Quantum computing in the future will be more of a threat. These highly-powered computers, as some brightest minds assume, may, one day, crack current hash algorithms and, thus, make it easier to reverse hashes or find collisions.
Because of this, researchers are already working on creating quantum-resistant algorithms that would stand up against new threats.
Proof-of-work systems rely heavily on hashing in mining, where miners try to outcompete one another by solving complex puzzles with hash generation.
Due to this fact, such a process consumes enormous energy; consequently, the environmental footprint of blockchains such as Bitcoin is starting to emerge as a concern.