Once used exclusively by the cybercriminals behind REVil ransomware and the Gootkit banking trojan, GootLoader and its primary payload have evolved into an initial access as a service platform—with Gootkit providing information stealing capabilities as well as the capability to deploy post-exploitation tools and ransomware.
GootLoader is known for using search engine optimization (SEO) poisoning for its initial access. Victims are often enticed into clicking on malicious adware or links disguised as legitimate marketing, or in this case a legitimate Google search directing the user to a compromised website hosting a malicious payload masquerading as the desired file. If the malware remains undetected on the victim’s machine, it makes way for a second-stage payload known as GootKit, which is a highly evasive info stealer and remote access Trojan (RAT) used to establish a persistent foothold in the victim’s network environment. GootKit can be used to deploy ransomware or other tools, including Cobalt Strike, for follow-on exploitation.
Detection of a new GootLoader variant actively being used by adversaries earlier this year led to a broad threat hunting campaign by Sophos X-Ops MDR for GootLoader instances across customer environments. As is typical of Gootloader, the new variant was found to be using SEO poisoning—the use of search engine optimization tactics to put malicious websites controlled by GootLoader’s operators high in the results for specific search terms—to deliver the new, JavaScript-based Gootloader package. In this case, we found the GootLoader actors using search results for information about a particular cat and a particular geography being used to deliver the payload: “Are Bengal Cats legal in Australia?”
During the threat hunt campaign, MDR discovered a .zip archive used to deliver GootLoader’s first-stage payload while reviewing an impacted user’s browser history. This allowed MDR to identify the compromised website that was hosting the malicious payload. This report highlights the MDR investigation process and the technical details of the uncovered GootLoader campaign.
Technical Analysis and Identification
First-stage payload
On March 27, 2024, the MDR team performed a proactive threat hunting campaign across multiple customers estates, following recently reported identification of a new GootLoader variant being actively exploited in the wild.
Our investigation revealed the threat actor was using SEO poisoning through an easily accessed online forum found via a simple Google search, initiated by the user for ‘Do you need a license to own a Bengal cat in Australia’. The first search result took us to this URL:
hxxps[://]ledabel[.]be/en/are-bengal-cats-legal-in-australia-understanding-the-laws-and-regulations/#:~:text=Each%20state%20and%20territory%20in,to%20keep%20them%20as%20pets.
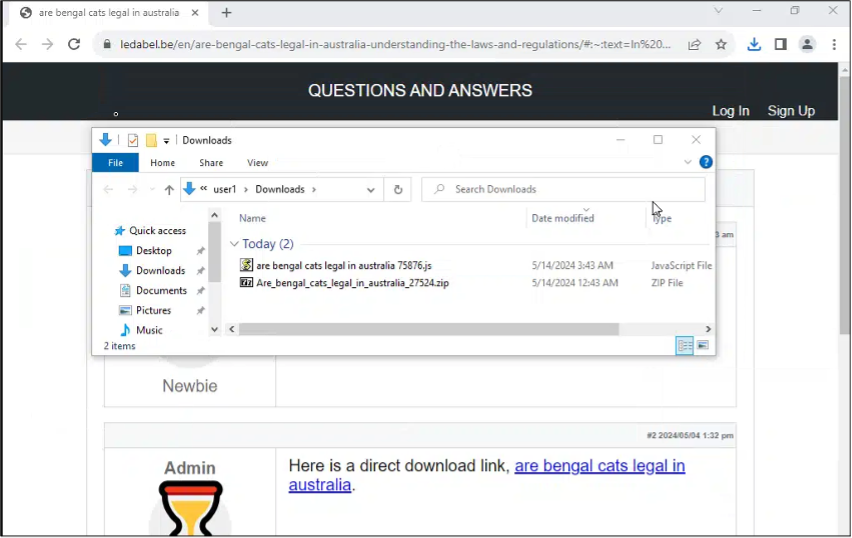
Immediately after the user clicks the link, a suspicious .zip file was downloaded to C:\Users\<Username>\Downloads\Are_bengal_cats_legal_in_australia_33924.zip onto the victim’s machine, and the user’s browser was directed to the URL hxxps:[//]www[.]chanderbhushan[.]com/doc[.]php.

Second-stage payload
Upon review of the running processes, we were able to determine that a small JavaScript file was dropping a large JavaScript file at the location C:\Users\<Username>\AppData\RoamingMicrosoft\ on the user’s machine. During our testing, the large JavaScript file generated by the malicious site and its name, downloaded to the user’s %temp% directory, were different each time the initial JavaScript was executed. The file we observed in this case was named Temp1_Are_bengal_cats_legal_in_australia_33924.zip\are_bengal_cats_legal_in_australia_80872.js.
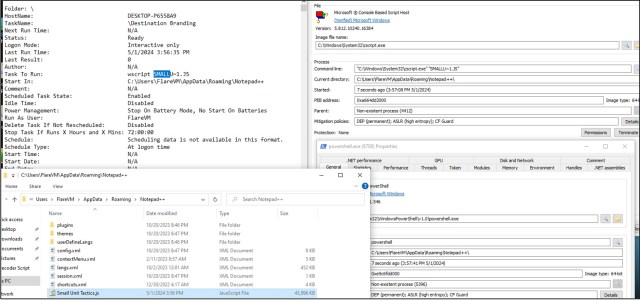
We additionally observed the creation of a scheduled task named “Business Aviation” with the command line “wscript REHABI~1.JS” (as shown in Figure 3). This was suspected to be a persistence method in which the threat actor was utilizing WScript.exe to execute the second-stage payload of GootKit.
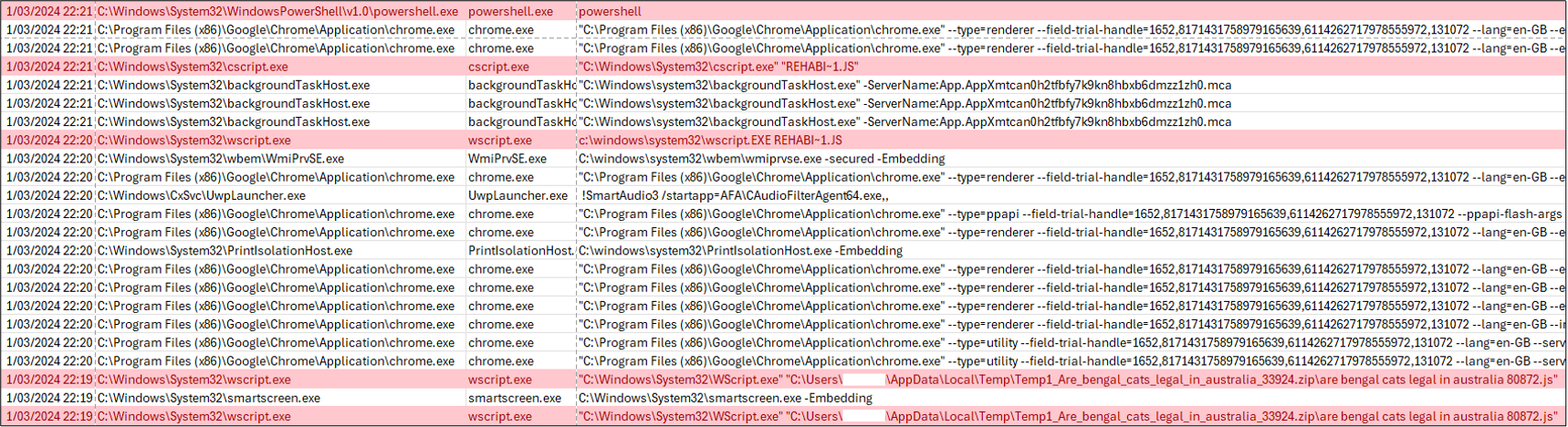

We also noted the utilization of the command C:\Windows\System32\cscript.exe REHABI~1.JS spawning PowerShell.exe, as shown in Figure 4. The cscript.exe command line tool is specific to Windows Server. The commands passed to PowerShell were not captured in this case.

However, examining the URL history, we observed PowerShell.exe reaching out to the following domains, as shown in Figure 5. Third-stage payload
In the case the MDR team examined, our team did not observe the third stage being successful in reaching a full deployment of GootKit, preventing the download of any additional malicious tooling. This stage typically is where the deployment of additional tools such as Cobalt Strike occurs, or when ransomware is added to the victim’s machine.
Malware Triage
Static Analysis
MDR performed a static analysis of the of the .zip sample obtained from the malicious URL hxxps[://]ledabel[.]be/en/are-bengal-cats-legal-in-australia-understanding-the-laws-and-regulations/#:~:text=In%20most%20cases%2C%20you%20do,a%20Bengal%20cat%20in%20Australia. Within the zip file was a JavaScript named “are bengal cats legal in australia 72495.js”.
As we noted above, the JavaScript’s name is modified each time the file is downloaded with a different concluding numerical sequence. This was also observed when extracting the small JavaScript from the zip file, as shown in Figure 6. For example, users may observe a filename with are bengal cats legal in australia 75876.zip instead, when attempting to obtain a sample from the malicious URL.
A string analysis of the dropped file was not useful in identifying its intent, as the JavaScript was heavily obfuscated—as is common in Gootloader samples. The script also included boilerplate licensing comments to make it appear to be a legitimate JavaScript, as shown in Figure 7.
However, Strings analysis of the secondary larger JavaScript that was downloaded into C:\Users\<Username>\AppData\Roaming\Notepad++\Small Unit Tactics.js revealed a heavily obfuscated script, as shown in Figure 8.

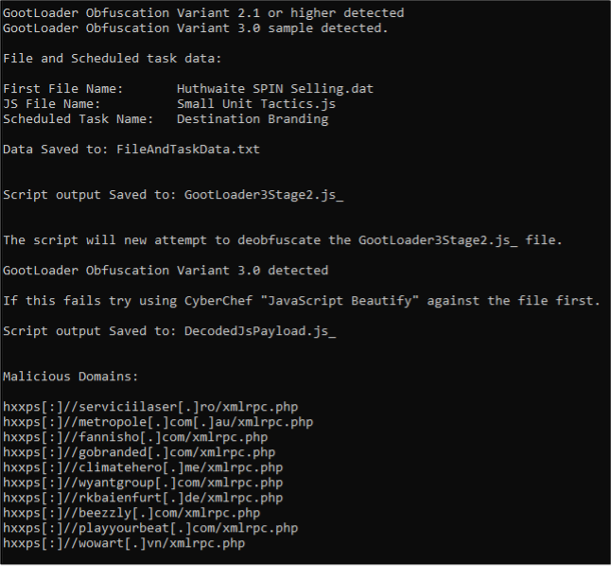
MDR used a Python script created by Mandiant for auto-decoding of GootLoader JavaScript to statically analyze the initially downloaded Are_bengal_cats_legal_in_australia_72495.js. As shown in Figure 9, the file was identified as Gootloader variant 3.0 through the obfuscation method, where the first file created was named Huthwaite SPIN selling.dat followed by Small Units Tactics.js and Scheduled Task named Destination Branding. The decoder also identified various malicious domain names within the obfuscated strings.
Dynamic analysis
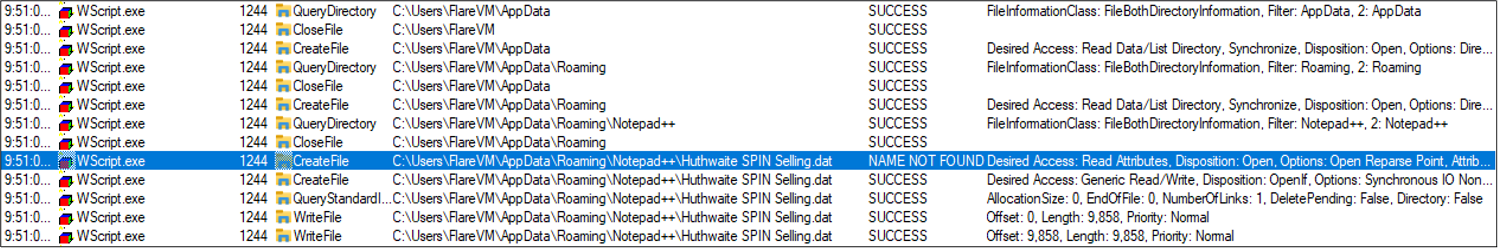
Various dynamic analysis tools were utilized to examine the behavior of the malicious JavaScript. Upon execution, WScript.exe was observed creating the first file located within C:\Users\<Username>\AppData\Roaming\Notepad++\ , as shown in Figure 10. Despite being observed via Windows Sysinternals Process Monitor with a CreateFile event, this was not written to disk and no deletion event was seen.
Shortly after Wscript.exe executed Are_bengal_cats_legal_in_australia_72495.js, Process Hacker showed CScript.exe and Powershell.exe being created with a conhost.exe spawned, as shown in Figure 11. MDR observed that Wscript.exe would terminate, followed by Cscript.exe that would also terminate shortly after, after which Powershell.exe was created.

Persistence was obtained via CScript.exe executing the file SMALLU~1.js via a scheduled task named Destination Branding (with command line wscript SMALLU ~1.js , as shown in Figure 12). During the lab analysis, the secondary JavaScript can be dropped within any folders located within C:\Users\<Username>\AppData\Roaming\<at any existing folder>.
MDR conducted network and C2 examinations using Wireshark and FakeNet to perform a network capture during the execution of Are_bengal_cats_legal_in_australia_72495.js. FakeNet showed various domain names being reached out to with GET /xmlrpc.php HTTP/1.1 requests via Powershell.exe. The requests contained Base64-encoded cookies which, when decoded, showed enumeration information regarding device directories and host information such as the folder path of C:\Users\<Username>\AppData\Roaming\ , as shown in Figure 13. As shown below, the process would read USERNAME and USER DOMAIN information and send the data to the URIs.
Examination of the PCAP capture lists various domain names that were also identified during static analysis, as shown in Figure 14. These domain names and IOCs have been classified by Sophos Labs as malware/callhome ; the initial and secondary JavaScript files are classified as JS/Drop-DIJ and JS/Gootkit-AW respectively.

MITRE mapping
The following chart maps the observed tactics to the MITRE ATT&CK® framework.
| Tactic | Technique | Sub-Technique | ID |
| Reconnaissance | |||
| Resource Development | Stage Capabilities | Upload Malware
SEO Poisoning |
T1608.001
T1608.006 |
| Initial Access | Drive-by Compromise | T1189 | |
| Execution | Command and Scripting Interpreter | JavaScript | T1059.007 |
| Persistence | Scheduled Task/Job | Scheduled Task | T1053.005 |
| Privilege Escalation | |||
| Defense Evasion | Obfuscated Files or Information | Embedded Payloads | T1027.009 |
| Credential Access | |||
| Discovery | System Information Discovery | T1082 | |
| Lateral Movement | |||
| Collection | |||
| Command and Control | |||
| Exfiltration | Exfiltration Over Web Service | T1567 | |
| Impact |
Conclusion
GootLoader is one of a number of continuing malware-delivery-as-a-service operations that heavily leverage search results as a means to reach victims. The use of search engine optimization, and abuse of search engine advertising to lure targets to download malware loaders and dropper, are not new—GootLoader has been doing this since at least 2020, and we’ve observed Raccoon Stealer and other malware-as-a-service operations doing the same for just as long. But we’ve seen continued growth in this approach to initial compromise, with several massive campaigns using this technique over the past year.
Sophos endpoint protection blocks GootLoader through a number of behavioral and malware-specific detections. But users should still look out for search results and search advertisements that seem too good to be true on domains that are off the beaten path—whether they’re looking to get a Bengal Cat or not.
Indicators of Compromise
A list of IOCs is available as a CSV file in the Sophos GitHub repository here.