

UnitedHealth has confirmed for the first time that over 100 million people had their personal information and healthcare data stolen in the Change Healthcare ransomware attack, marking this as the largest healthcare data breach in recent years.
In May, UnitedHealth CEO Andrew Witty warned during a congressional hearing that “maybe a third” of all American’s health data was exposed in the attack.
A month later, Change Healthcare published a data breach notification warning that the February ransomware attack on Change Healthcare exposed a “substantial quantity of data” for a “substantial proportion of people in America.”
Today, the U.S. Department of Health and Human Services Office for Civil Rights data breach portal updated the total number of impacted people to 100 million, making it the first time UnitedHealth, the parent company of Change Healthcare, put an official number to the breach.
“On October 22, 2024, Change Healthcare notified OCR that approximately 100 million individual notices have been sent regarding this breach,” reads an updated FAQ on the OCR website.
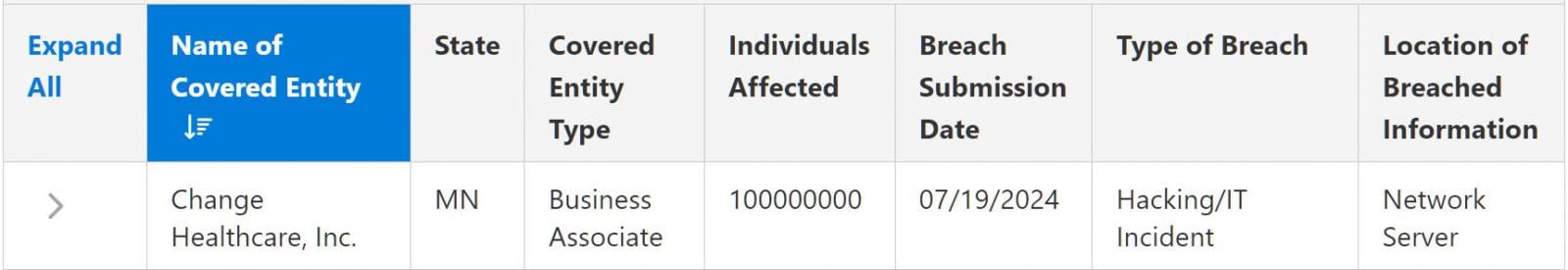
Source: HHS
Data breach notifications sent by Change Healthcare since June state that a massive amount of sensitive information was stolen during the February ransomware attack, including:
- Health insurance information (such as primary, secondary or other health plans/policies, insurance companies, member/group ID numbers, and Medicaid-Medicare-government payor ID numbers);
- Health information (such as medical record numbers, providers, diagnoses, medicines, test results, images, care and treatment);
- Billing, claims and payment information (such as claim numbers, account numbers, billing codes, payment cards, financial and banking information, payments made, and balance due); and/or
- Other personal information such as Social Security numbers, driver’s licenses or state ID numbers, or passport numbers.
The information may be different for each individual, and not everyone’s medical history was exposed.
The Change Healthcare ransomware attack
This data breach was caused by a February ransomware attack on UnitedHealth subsidiary Change Healthcare, which led to widespread outages in the U.S. healthcare system.
The disruption to the company’s IT systems prevented doctors and pharmacies from filing claims and prevented pharmacies from accepting discount prescription cards, causing patients to pay full price for medications.
The BlackCat ransomware gang, aka ALPHV, conducted the attack, using stolen credentials to breach the company’s Citrix remote access service, which did not have multi-factor authentication enabled.
During the attack, the threat actors stole 6 TB of data and ultimately encrypted computers on the network, causing the company to shut down IT systems to prevent the spread of the attack.
The UnitedHealth Group admitted to paying a ransom demand to receive a decryptor and for the threat actors to delete the stolen data. The ransom payment was allegedly $22 million, according to the BlackCat ransomware affiliate who conducted the attack.
This ransom payment was supposed to be split between the affiliate and the ransomware operation, but the BlackCat suddenly shut down, stealing the entire payment for themselves and pulling an exit scam.
However, this wasn’t the end of Change Healthcare’s problems, as the affiliate claimed they still had the company’s data and did not delete it as promised. The affiliate partnered with a new ransomware operation named RansomHub and began leaking some of the stolen data, demanding an additional payment for the data not to be released.
The entry for Change Healthcare entry on RansomHub’s data leak site mysteriously disappeared a few days later, possibly indicating that United Health paid a second ransom demand.
UnitedHealth said in April that the Change Healthcare ransomware attack caused $872 million in losses, which increased as part of the Q3 2024 earnings to an expected $2.45 billion for the nine months to September 30, 2024,