

Multiple popular mobile applications for iOS and Android come with hardcoded, unencrypted credentials for cloud services like Amazon Web Services (AWS) and Microsoft Azure Blob Storage, exposing user data and source code to security breaches.
Exposing this type of credentials can easily lead to unauthorized access to storage buckets and databases with sensitive user data. Apart from this, an attacker could use them to manipulate or steal data.
According to a report from Symantec, a Broadcom company, these keys are present in the apps’ codebases because of errors and bad practices during the development phase.
“Recent analysis has uncovered a troubling trend: several widely-used apps have been found to contain hardcoded and unencrypted cloud service credentials within their codebases,” Symantec explains.
“This dangerous practice means that anyone with access to the app’s binary or source code could potentially extract these credentials and misuse them to manipulate or exfiltrate data, leading to severe security breaches,” the researchers say.
Symantec says that its reasearchers found credentials to cloud services in the following apps on Google Play:
- Pic Stitch – 5M+ downloads – Amazon hardcoded credentials
- Meru Cabs – 5M+ downloads – Microsoft Azure Blob Storage hardcoded credentials
- Sulekha Business – 500K+ downloads – Microsoft Azure Blob Storage hardcoded credentials
- ReSound Tinnitus Relief – 500K+ downloads – Microsoft Azure Blob Storage hardcoded credentials
- Saludsa – 100K+ downloads – Microsoft Azure Blob Storage hardcoded credentials
- Chola Ms Break In – 100K+ downloads – Microsoft Azure Blob Storage hardcoded credentials
- EatSleepRIDE Motorcycle GPS – 100K+ downloads – Twilio hardcoded credentials
- Beltone Tinnitus Calmer – 100K+ downloads – Microsoft Azure Blob Storage hardcoded credentials
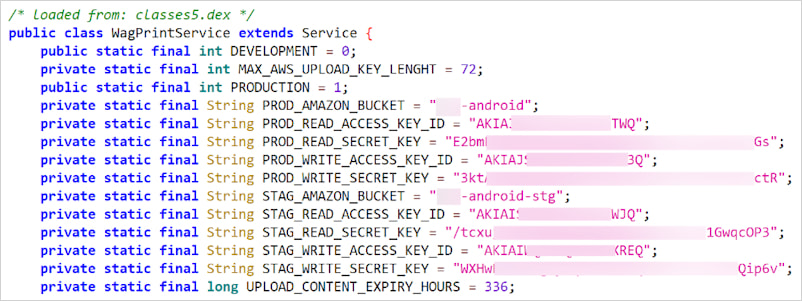
Source: Symantec
They also discovered credentials in several popular apps listed in Apple’s App Store:
- Crumbl – 3.9M+ ratings – Amazon hardcoded credentials
- Eureka: Earn money for surveys – 402.1K+ ratings – Amazon hardcoded credentials
- Videoshop – Video Editor – 357.9K+ ratings – Amazon hardcoded credentials
- Solitaire Clash: Win Real Cash – 244.8K+ ratings – Amazon hardcoded credentials
- Zap Surveys – Earn Easy Money – 235K+ ratings – Amazon hardcoded credentials
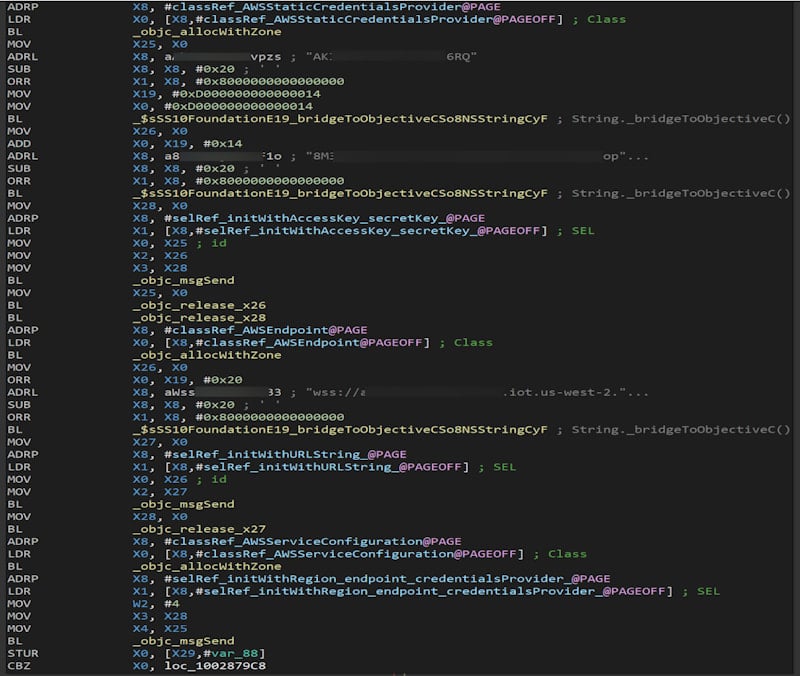
Source: Symantec
While the App Store does not report the number of downloads, the number is typically much higher than the amount of ratings listed.
It is worth noting that Google displays in Play Store the total number of downloads for the lifetime of the app and does not reflect active installations.
The presence of any of the apps above on your phone does not mean that your personal data has been stolen but that it is accessible and hackers could exfiltrate it unless developers take action and remove the risk.
In September 2022, Symantec raised the alarm about this risk, highlighting that its researchers found more than 1,800 iOS and Android apps that contained AWS credentials, 77% of the apps having valid access tokens in the codebase.
The researchers recommend developers to follow best practices for protecting sensitive information in mobile apps.
This includes using environment variables to store credentials, using secrets management tools (e.g. AWS Secrets Manager, Azure Key Vault), encrypting data, regular code reviews and audits, and integrate automated security scanning early in the development process to detect sensitive data or security issues.