
Cyber-enabled fraud, innovative criminal organizations, and advances in money laundering have created a booming shadow economy in Southeast Asia that grows more entrenched every year, creating challenges for governments in the region.
The criminal syndicates in the delta region of the Mekong River and the greater Asia-Pacific region operate out of casinos, hotels, special economic zones, and other properties, which have become hubs for massive cybercriminal enterprises, raking in between $27 billion and $37 billion a year in profits, according to a report published on Oct. 7 by the United Nations Office on Drugs and Crime (UNODC). While some law enforcement organizations and regional officials have mounted efforts to fight against the growing criminal syndicates, they often just move their operations to “inaccessible and autonomous non-state armed group territories and other criminal enclaves,” the report stated.
The result is a cybercrime-induced crisis, where the profits are driving quick innovation in criminal professionalization, money laundering, and forced labor and human trafficking, John Wojcik, a regional analyst with the UNODC, said in an email interview.
“It is now increasingly clear that a potentially irreversible shift has taken place in which organized crime are able to target countries globally at an unprecedented scale while picking jurisdictions and moving criminal proceeds as needed, with the resulting situation rapidly outpacing the capacity of governments to contain it,” he said.
The UNODC report — “Transnational Organized Crime and the Convergence of Cyber-Enabled Fraud, Underground Banking and Technological Innovation in Southeast Asia: A Shifting Threat Landscape” — is the latest update on the growing cybercrime ecosystem undermining economic development and human rights in Southeast Asia. The UNODC analysts estimated that victims in East and Southeast Asia had lost $18 billion to $37 billion due mainly to organized crime group. Globally, the groups have garnered between $27 billion and $37 billion, with experimentation with generative AI technology likely to lead to greater losses as a “force multiplier,” USODC’s Wojcik said.
The regional troubles are partly due to the geopolitics and the international rivalries in the region, which spilled over to the cyberspace domain, says Vishal Gupta, CEO of data-security firm Seclore. Operatives and hackers trained for that cyber conflict have either created their own cybercriminals groups or joined already existing crime syndicates, says Gupta, who has conducted business in the region for years.
“This ecosystem just didn’t pop up, you know, all of a sudden,” he says. “If you consider any of the nations — Malaysia, Thailand, Indonesia, and so on outside of China, which is the 800-pound gorilla over there — but if you look at any of these nations, there is very little collaboration with others … and cybercriminals are using that to their benefit.”
Corruptions and Lax Legal Frameworks
Most of the cybercriminal groups operate in the nations in the Mekong delta region — including Cambodia, Laos, and Myanmar — but have shown their ability to move to ungoverned regions or those with friendly governments.
The massive scale of profits — $37 billion is more than 7% of the GDP of those three nations — has driven the professionalization and innovation of money laundering, linking transnational criminal groups in Southeast Asia, which have emerged as global market leaders, UNODC’s Wojcik said.
“Asian crime syndicates have effectively established and streamlined a parallel banking system capable of laundering and integrating vast amounts of illicit proceeds into the formal financial system undetected,” he said. “The sophistication of these methods at this scale is something we have not seen before.”
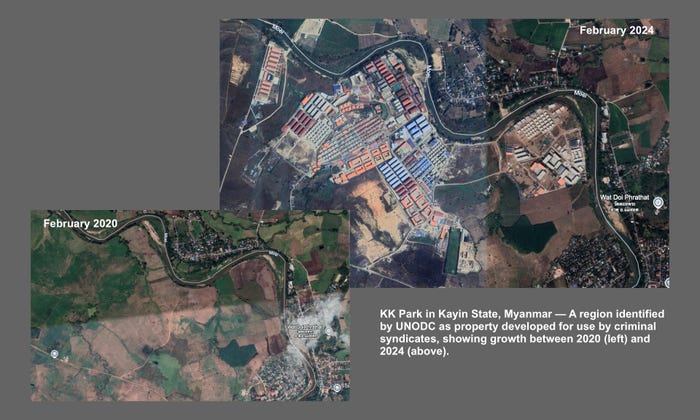
Source: Author created graphic using Google Earth historical maps of region identified by UNODC
The economic growth fueled by the cybercriminal boom in nothing short of astonishing. In one area of Myanmar across the river from Thailand, a town-sized compound with advanced internet communications technology (ICT) infrastructure has appeared over the past five years, according to the UNODC report.
The technical ability for criminal syndicates has outpaced businesses and other regional organizations, Seclore’s Gupta says.
“The pace at which the criminals are innovating [and] the pace at which companies are innovating — that pace has been different,” he says. “The criminals are innovating on a daily basis, and companies are innovating with their defenses on a monthly or a quarterly or sometimes on an annual basis.”
Not Just “Pig Butchering”
The cybercriminals have also diversified their income. While “pig butchering” has garnered the most media attention, the long-con cybersecurity scam — where a fraudster makes contact with the victim, gains their trust, and then cashes out by convincing them to invest through a seemingly legitimate financial service — is just one of the weapons in a cybercriminal syndicate’s arsenal.
While casinos and online gambling are the foundation for the groups profits, law enforcement authorities have encounter a burgeoning menagerie of cybercriminal techniques that lead back to Southeast Asian crime syndicates, UNDOC’s Wojcik said. Information-stealing malware, ransomware, and impersonation and kidnapping scams — increasingly with deepfake components — have become common, he said.
“There is growing concern that Asian crime syndicates are rapidly maturing into more sophisticated cyber-threat actors, aided by technological advancements that have not only expanded the scope and efficiency of cyber-enabled fraud and cybercrime but have also lowered the barriers to entry for criminal networks that previously lacked the technical skills to exploit more sophisticated and profitable methods,” Wojcik said.
Secore’s Gupta has a more positive outlook.
“The chances that a year from now we will see better cooperation, more stringent laws, the equivalent of digital embargoes that I described and so on, will be better than today, I think, is very high,” he says. “I see that happening, and countries are clamping down on all of these operations. So if you look at the number of raids and cyber investigation infrastructure that has been created by each of the countries in just the three, four years of COVID, it’s gone up.
“There are positive signs,” he says. “I think the nations are finally coming to a realization that if they breed snakes, then at some stage, the snake is going to come back and bite the breeder.”