

A malware campaign uses the unusual method of locking users in their browser’s kiosk mode to annoy them into entering their Google credentials, which are then stolen by information-stealing malware.
Specifically, the malware “locks” the user’s browser on Google’s login page with no obvious way to close the window, as the malware also blocks the “ESC” and “F11” keyboard keys. The goal is to frustrate the user enough that they enter and save their Google credentials in the browser to “unlock” the computer.
Once credentials are saved, the StealC information-stealing malware steals them from the credential store and sends them back to the attacker.
Kiosk mode theft
According to OALABS researchers who uncovered this peculiar attack method, it has been used in the wild since at least August 22, 2024, mainly by Amadey, a malware loader, info-stealer, and system reconnaissance tool first deployed by hackers in 2018.
When launched, Amadey will deploy an AutoIt script that acts as the credentials flusher, which scans the infected machine for available browsers and launches one in kiosk mode to a specified URL.
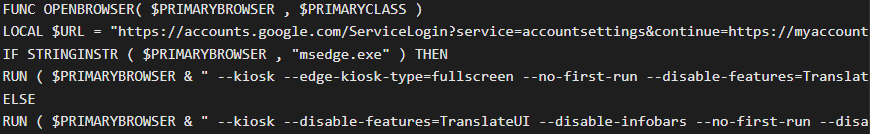
Source: OALABS
The script also sets an ignore parameter for the F11 and Escape keys on the victim’s browser, preventing an easy escape from the kiosk mode.
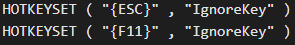
Source: OALABS
Kiosk mode is a special configuration used in web browsers or apps to run in full-screen mode without the standard user interface elements like toolbars, address bars, or navigation buttons. It’s designed to limit user interaction to specific functions, making it ideal for public kiosks, demonstration terminals, etc.
In this Amadey attack, though, kiosk mode is abused to restrict user actions and limit them to the login page, with the only apparent choice being to enter their account credentials.
For this attack, the kiosk mode will be opened to https://accounts.google.com/ServiceLogin?service=accountsettings&continue=https://myaccount.google.com/signinoptions/password, which corresponds to the change password URL for Google accounts.
As Google requires you to reenter your password before it can be changed, it provides an opportunity for the user to reauthenticate and potentially save their password in the browser when prompted.
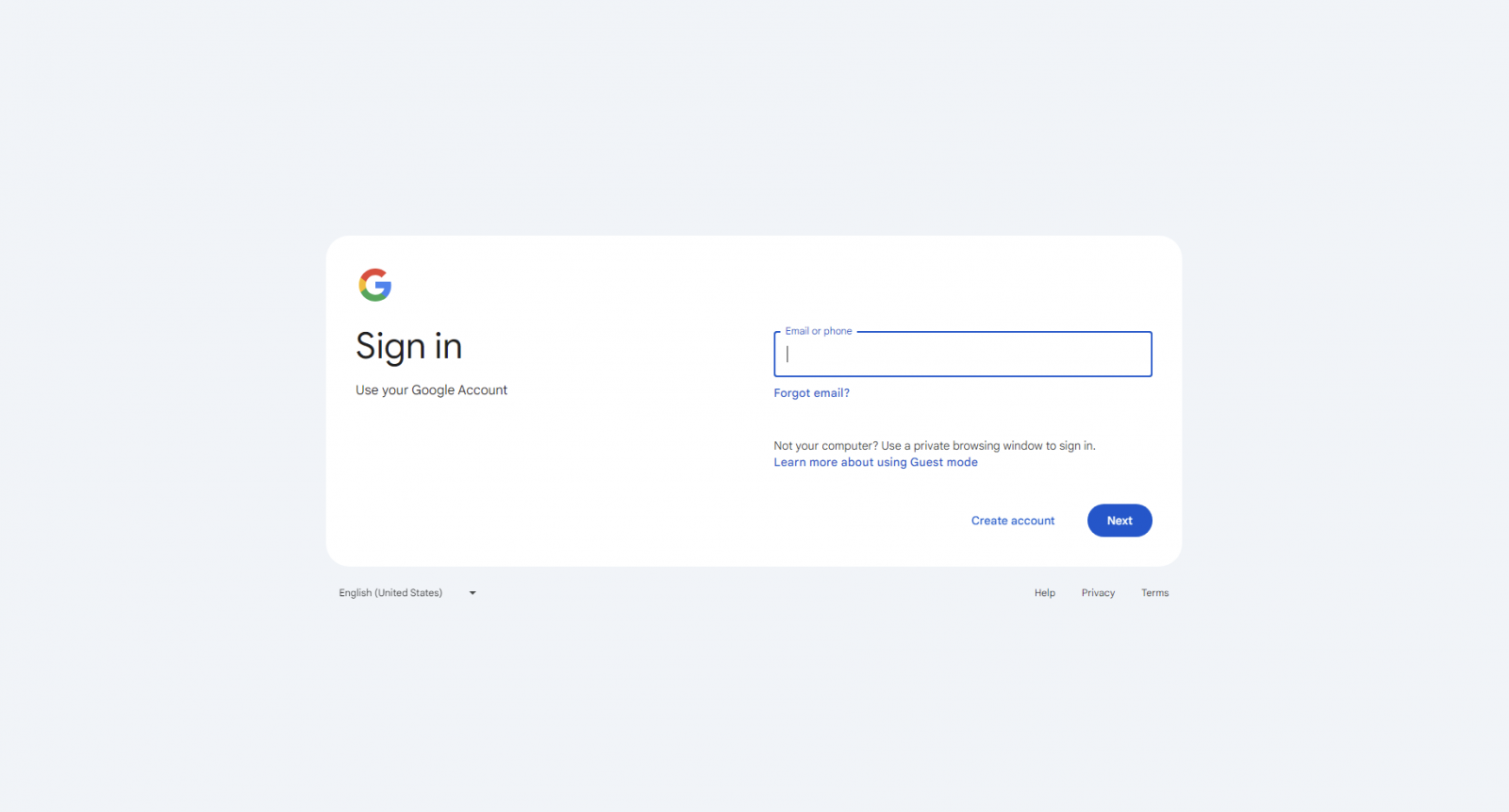
Source: OALABS
Any credentials the victim enters on the page and then saves to the browser when prompted are stolen by StealC, a lightweight and versatile information stealer launched in early 2023.
Exiting the kiosk mode
Users who find themselves in the unfortunate situation of getting locked in kiosk mode, with Esc and F11 not doing anything, should keep their frustration in check and avoid entering any sensitive information on forms.
Instead, try other hotkey combos like ‘Alt + F4’, ‘Ctrl + Shift + Esc’, ‘Ctrl + Alt +Delete’, and ‘Alt +Tab.’
Those may help bring the desktop on the foreground, cycle through open apps, and launch the Task Manager to terminate the browser (End Task).
Pressing ‘Win Key + R’ should open the Windows command prompt. Type ‘cmd’ and then kill Chrome with ‘taskkill /IM chrome.exe /F.’
If all else fails, you can always perform a hard reset by holding the Power button until the computer shuts down. This may result in losing unsaved work, but this scenario should still be better than having account credentials stolen.
When rebooting, press F8, select Safe Mode, and once you’re back on the OS, run a full antivirus scan to locate and remove the malware. Spontaneous kiosk mode browser launches are not normal and shouldn’t be ignored.