
Recent investigations into the cyber security preparedness of Australian Federal Government agencies have found gaps in the public sector’s readiness for cyber security attacks or major data breaches, contributing to a focus in 2024 on improving their cyber readiness.
An audit of two government agencies, Services Australia and AUSTRAC, released in 2024, revealed these agencies are not well-prepared to recover from a significant cyber attack, while a previous whole-of-government survey found gaps in some areas of agency cyber maturity.
The Australian Government’s Cyber Security Strategy 2023-2030 said the Federal Government should “hold itself to the same standard it expects of industry.” In 2024, a focus of the Australian Signals Directorate is to uplift cybersecurity skills in government agencies.
Australian government entities unfit for heightened cyber threat environment
Australian public sector agencies are prime targets for cybercriminals because of the data they hold. For instance, the Australian Taxation Office revealed in 2024 that it faces 4.7 million attacks per month due to the 50 petabytes of data it holds, while data on a significant number of people was accessed when South Australian super fund operator Super SA was compromised in 2023.
Attacks faced by Australian government entities in 2022-23
Official statistics based on incidents reported to the ASD show that government entities continue to prove attractive targets for cybercriminals, with a strong volume of attacks. In 2022-2023:
- Approximately 31% of cyber security incidents reported to the Australian Signals Directorate were from Australian Government entities.
- Over 40% of these were coordinated low-level malicious cyberattacks directed at the federal government, government-shared services or regulated critical infrastructure.
- Ransomware is the most significant cybercrime threat, posing considerable risk to Australian Government entities as well as businesses and individuals.
SEE: Will Australia ever dig itself out of the cyber security skills shortage?
The current cyber security posture of government entities
The ASD’s 2023 Cyber Security Posture Report, assessing the maturity level of all government agencies, indicated that “the overall maturity level across entities remained low in 2023.” The report found:
- 25% of entities self-assessed at Maturity Level Two across the ASD’s Essential Eight mitigation strategies. The Essential Eight framework includes four maturity levels, with Maturity Level Zero the lowest and Level Three considered best practice.
- Most public sector entities — 71% — self-assessed at Maturity Level Two for the Essential Eight mitigation strategy “Regular backups.” This indicated a potential problem with the ability to recover from a significant cyberattack.
- Just 82% had an incident response plan, though this was an improvement from 2022. Of these, 90% said that their plan had been last updated within the last two years, and 69% indicated it had been enacted at least every two years.
Previous audits of public sector bodies, including the Australian Federal Police, Australian Taxation Office and Department of Foreign Affairs and Trade, conducted by the Australian National Audit Office, had also “identified low levels of cyber resilience in entities.”
AUSTRAC, Services Australia show cyber security deficiencies
An ANAO report on cyber security incident management at Services Australia and AUSTRAC in June 2024 found their measures only “partially effective,” with neither well placed to ensure business continuity or disaster recovery after a significant cyber security incident.
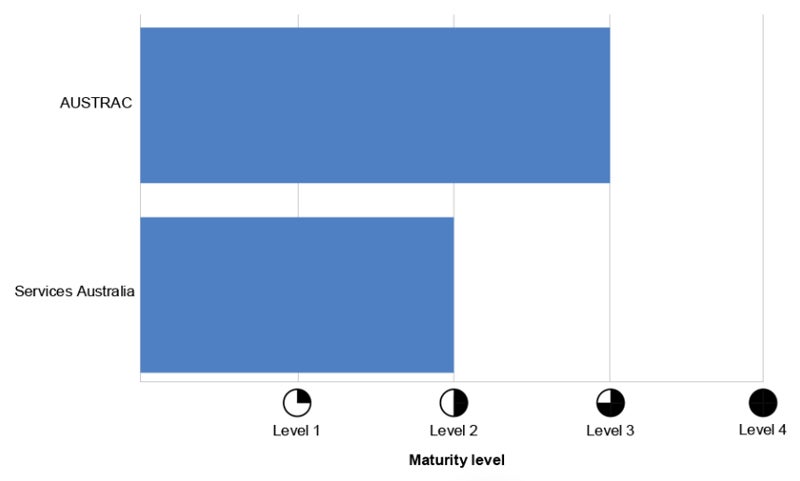
Services Australia, delivering services and payments to citizens, and AUSTRAC, responsible for stopping criminal abuse of the financial system, are both custodians of economic or commercial information and personal information, and are classed as national security or critical infrastructure.
AUSTRAC
The ANAO report found that AUSTRAC’s procedures supporting incident recovery processes did not include the security and testing of backup solutions, nor did they detail the systems, applications and servers supporting critical business processes.
In addition, it did not detail CISO responsibilities — its continuous monitoring and improvement reporting approach — or define timeframes for reporting. Further, the organisation did not have an event logging policy or document its analysis of all cyber security events, violating ASD guidelines.
SEE: CISOs in Australia urged to take a closer look at data breach risks
Services Australia
Services Australia is only “partly effective” in the design of cyber security incident management procedures, with no documented approach to threat and vulnerability assessments. It also had no timeframe for triage and escalation, and no defined approach for investigations.
The agency had “partly implemented effective recovery processes,” including regular backups. However, its plans did not include all systems and applications supporting critical business processes, and the agency does not test the recoverability of backups.
What is the Australian national cyber security strategy?
The Australian government is aware of the need for agencies to improve their level of cyber security preparedness and resilience. In the Cyber Security Strategy 2023-2030, for example, the government writes that, as an owner and operator of critical infrastructure and being responsible for holding some of the most sensitive data about Australia’s people, economy and national security, “the government needs to hold itself to the same standard it imposes on industry.”
As part of the strategy, the government has committed to:
- Strengthening the cyber maturity of government departments and agencies.
- Identifying and protecting critical systems across government.
- Uplifting the cyber skills of the Australian Public Service.
The ASD said it is playing a role in stepping up security at government agencies in 2024 using extra funding. This includes introducing more technical capabilities to departments and providing more experts to help agencies fortify their networks against cyber criminals.
Private sector demands rise in public sector security standards
The private sector will welcome moves to improve cyber security in the public sector.
In a recent submission to government on proposed cyber security legislative reforms, The Technology Council of Australia, representing the technology industry, urged the Australian government to uplift and safeguard its own information security practices and methods. This is to ensure that any information provided to it by private sector organisations, as part of mandatory cyber incident information sharing proposals, occurs in secure transfer environments and channels.
Amazon Web Services suggested the government should formally include its own critical infrastructure and “Systems of Government Significance” under the remit of the Security of Critical Infrastructure Act, or other legislative framework.
“Doing so would set important enforceable benchmarks for government,” AWS wrote, “and send an important signal to industry that government truly sees itself as an equal partner in the nation’s cyber uplift.”